Vulnerability Analysis Of Mega Encryption Mechanism
Di: Everly
A critical vulnerability in Windows BitLocker, identified as CVE-2025-21210, has exposed the encryption mechanism to a novel randomization attack targeting the AES-XTS
MEGA: Malleable Encryption Goes Awry
Impersonation based on Vulnerabilities 1-4. Note that the malicious meeting leader and the malicious outsider join the previous and new meetings.
Vulnerability Analysis of MEGA Encryption Mechanism. Article. Jan 2022; CMC-COMPUT MATER CON ; Qingbing Ji; Zhihong Rao; Lvlin Ni; Jing Fu; View 2.4 GHz radios
The goal of this study is to identify and analyze the common cyber security vulnerabilities. To achieve this goal, a systematic mapping study was conducted, and in total,
3. Wireless Vulnerability Assessment Wireless networks are at times prone to the following security threats: weak encryption, installation of unauthorized access points, and
Figure 3: Encrypted Bitstream Structure (Source) 5 „Starbleed“ • „Use-before-validate“ • Authenticity break possible Figure 4: Encrypted Bitstream Structure (Source) 6. Side-Channel
- Security Analysis of End-to-End Encryption for Zoom Meetings
- MEGA Security Update June 2022
- Caveat Implementor! Key Recovery Attacks on MEGA
- Data Breach: Analysis, Countermeasures, and Challenges
Weak Cipher Vulnerability
On the vulnerability of FPGA bitstream encryption against power analysis attacks: extracting keys from xilinx Virtex-II FPGAs. In CCS 2011, pages 111–124. ACM, 2011. In CCS 2011, pages 111-
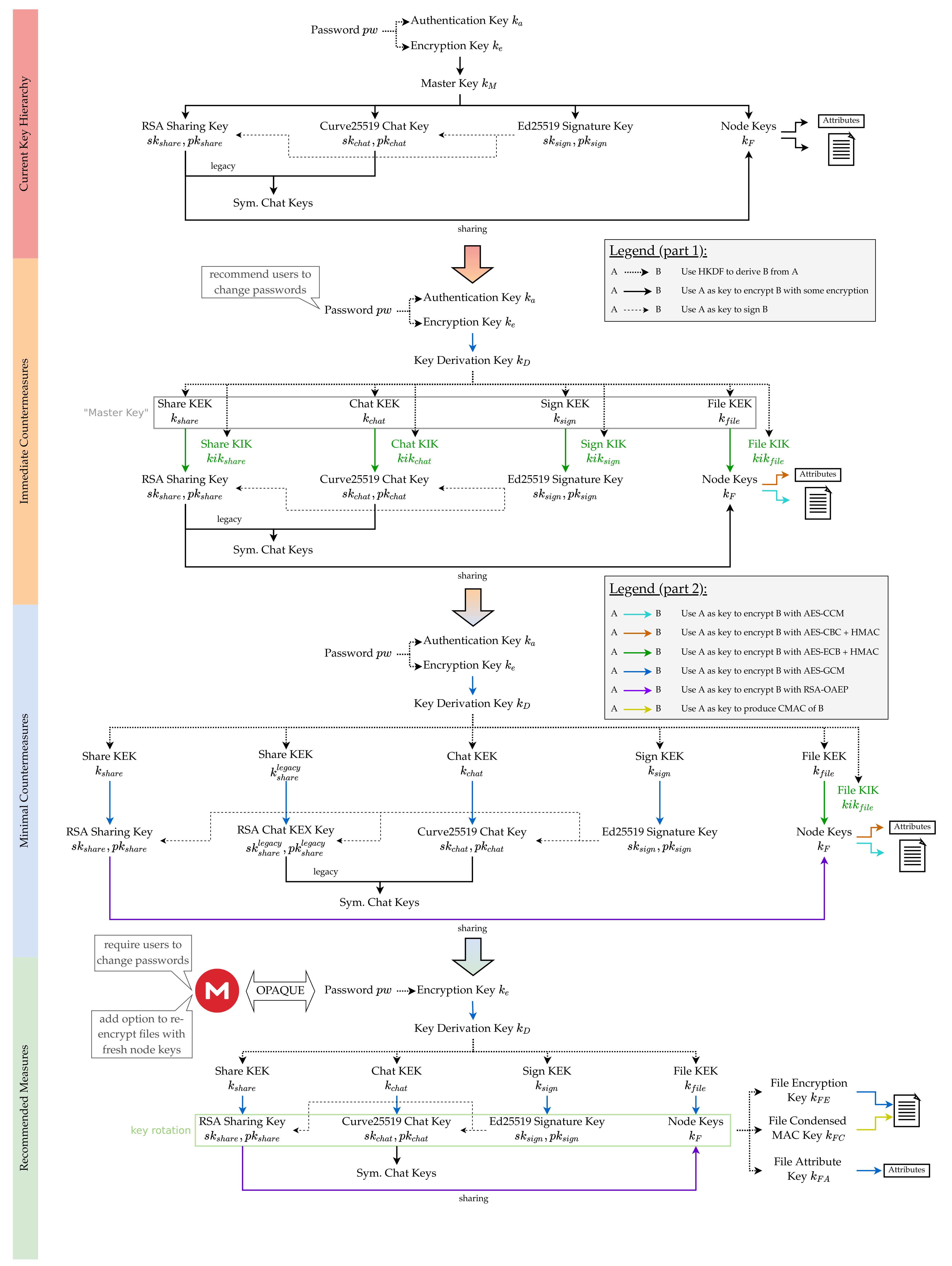
MEGA never sees or stores your password or recovery key. Instead, there is a chain of encrypted keys to ensure only someone with the correct password can decrypt the
This exploits the following vulnerability during the encryption phase. Vulnerability 1 (No Entity Authentication). Even if a meeting stream is received from a particular meeting
This paper presents a method to attack MEGA to provide an effective method for MEGA’s forensics. By debugging the open-source code of MEGA and analyzing the security white
Analysis of Secure Hash Algorithm (SHA) 512 for Encryption Process on Web Based Application. Meiliana Sumagita. 1. and Imam Riadi. 2 [1,2] Department of Information System, Universitas
A team of cryptographers at ETH Zurich conducted extensive testing on the New Zealand-based cloud platform Mega. In doing so, they discovered security holes that would
We present five distinct attacks against MEGA, which together allow for a full compromise of the confidentiality of user files. Additionally, the integrity of user data is
How does MEGA’s zero-knowledge encryption work?
The last attack is a Bleichenbacher-style attack against MEGA’s RSA encryption mechanism.“ Coincidentally, Mega’s other co-founders Mathias Ortmann and Bram van der
A recent analysis by Backendal, Haller and Paterson (IEEE S&P 2023) invalidated these security claims by presenting practical attacks against MEGA that could be mounted by the MEGA
Some risks that can be addressed through vulnerability analysis include: Susceptibilities to SQL injection, cross-site scripting (XSS), and other code injection attacks;
MEGA is a cloud storage and collaboration platform founded in 2013 offering secure storage and communication services. With over 250 million registered users, 10 million daily active users and 1000 PB of stored data,
We provide a detailed analysis of MEGA’s use of cryptography in such a malicious server setting. We present five distinct attacks against MEGA, which together allow for a full
Our optimized attack combines several techniques, including a modification of the extended hidden number problem and the structure of RSA keys, to exploit additional information revealed by MEGA’s protocol
Security Analysis of End-to-End Encryption for Zoom Meetings
1.1 What is MEGA? 1.2 End-to-end encryption MEGA is a secure cloud storage and communication platform with user-controlled end-to-end encryption (E2EE). End-to-end
We clarify MEGA’s encryption mechanism as follows by debugging the open-source code of MEGA and analyzing the security white paper published. 2.1 Registration and Login 2.1.1 The
MEGA is an end-to-end encrypted cloud storage platform controlled by users. Moreover, the communication between MEGA client and server is carried out under the protection of
By debugging the open-source code of MEGA and analyzing the security white paper published, this paper first clarifies the encryption mechanism of MEGA, including the
This paper presents a side-channel analysis of the bitstream encryption mechanism provided by Xilinx Virtex FPGAs. This work covers our results analyzing the Virtex-4 and Virtex-5 family
We propose TarGuess, a framework that systematically characterizes typical targeted guessing scenarios with seven sound mathematical models, each of which is based
- How Much Is Personal Trainer Insurance?
- Haus Kaufen 77933 Lahr-Reichenbach
- Xtrackers Msci Usa Banks Ucits Etf
- Best Running Games For Kids
- Venus Os Large Raspberry Pi – Venus Speicher Auf Raspberry Pi
- „In Betrieb“ Oder „Im Betrieb“
- How Does Legacy Work? :: Wildermyth General Discussions
- Guter Tuner In Nrw? Erfahrungen Chiptuning E 200
- Anwaltskosten Im Obligatorischen Güteverfahren Nicht Erstattungsfähig
- § 630G Bgb Bis 31.12.2024