Ship Windows Event Logs With Winlogbeat
Di: Everly
i’d like to ship winlogbeat as a sibling/sidecar container to an app container to ship an app’s event logs, rather than as a windows service running within the app container. this
Download Winlogbeat, the open source tool for shipping Windows event logs to Elasticsearch to get insight into your system, application, and security information.
Windows Defender via Winlogbeat
Love Windows? Winlogbeat helps you ship Windows event logs to Elasticsearch (or Logstash) in a lightweight way for analysis and tracking.
Learn the steps to integrate a Windows machine with Elastic Stack using Winlogbeat. Install, configure, and create dashboards in Kibana for real-time analysis of Windows event logs |
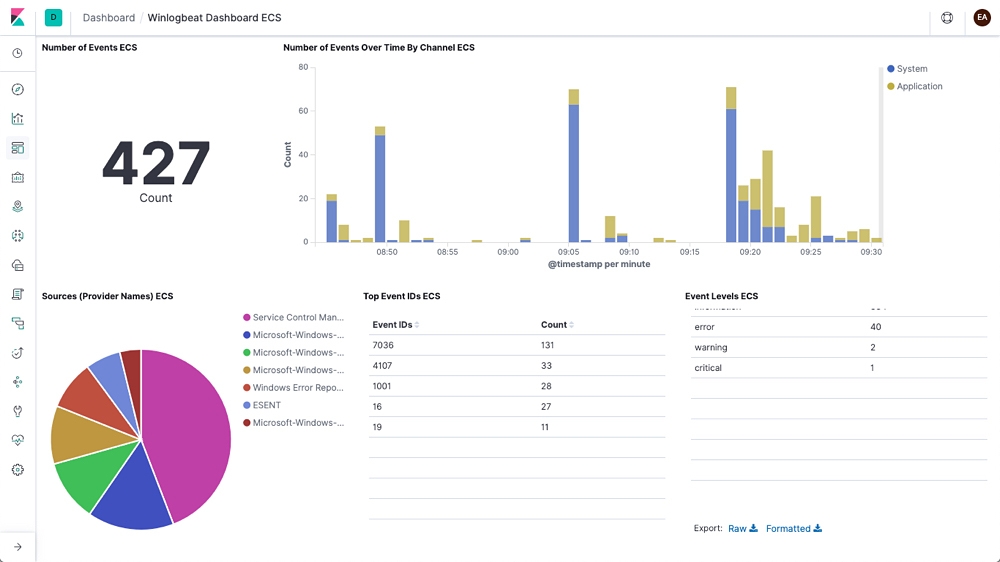
Winlogbeat is our lightweight shipper for Windows event logs. It installs and runs as a Windows service and ships event log data to Elasticsearch or Logstash. We will install
- Sending Windows Logs using WinLogbeat
- Learn How to Integrate and Configure Winlogbeat to Send Sysmon Logs
- Winlogbeat forwarding options · Security-Onion-Solutions
- Windows Defender via Winlogbeat
Winlogbeat is a Windows-specific event log-shipping agent. For more information about Powershell execution policies see here (opens in a new tab). If you have chosen to download
I installed Winlogbeat agent on my client servers and it works pretty good with windows event logs. I want to go further and ship logs from log files (for example
How to send logs to logstash through winlogbeat
This Windows log records system events that are sent by Windows and Windows system services, and are classified as error, warning, or information. Forwarded Events. This
Winlogbeat ships Windows event logs to Elasticsearch or Logstash. You can install it as a Windows service. Winlogbeat reads from one or more event logs
Hello, I’m working on a ELK server to monitor a windows server 2008 R2 farm. I installed Winlogbeat agent on my client servers and it works pretty good with windows event
Winlogbeat was developed specifically in order to ship Windows event logs to the Elasticsearch and Logstash engines, and it can be deployed as a standard service. The main
- Winlogbeat: connection to OpenSearch 2.0.0 doesn’t work
- Videos von Ship windows event logs with winlogbeat
- Sending Windows Event Viewer logs w/o using Winlogbeat
- Ingest Windows Event Logs
- Ship Windows event logs with Winlogbeat
Windows Sysmon (System Monitor) is a powerful logging tool designed to monitor and log system activity to the Windows event log. An extension of the Windows Event Logging system,
In this article, I will discuss how to ingest the Event Logs and IIS logs from Windows Server to OCI Search Service with OpenSearch. My preferred approach is to use the
Download Winlogbeat, the open source tool for shipping Windows event logs to Elasticsearch to get insight into your system, application, and security information.
I collect and ship logfiles from many systems, like Linux servers and network elements, which is easy with Syslog. But I also have some Windows systems, and I want to have the event logs collected and shipped to my
Download Winlogbeat, the open source tool for shipping Windows event logs to Elasticsearch to get insight into your system, application, and security information.
Ingest Windows event logs into Graylog using collectors like Winlogbeat or NXLog. Configure collectors, use Graylog inputs such as beats or GELF, and customize fields for efficient log
We will add the following under winlogbeat.event_logs: winlogbeat.event_logs: – name: Security event_id: 1102,4608,4609,4624-4648, 4700-4800,4950 ignore_older: 72h –
The winlogbeat section of the winlogbeat.yml config file specifies all options that are specific to Winlogbeat. Most importantly, it contains the list Docs. Release notes Troubleshoot
Winlogbeat is an open-source log collector that ships Windows Event Logs to Elasticsearch or Logstash. In this course, you will learn the setup, configuration, and validation
The following shows a base configuration that can be used which will ship logs from Application, System, Security, and Microsoft-Windows-Sysmon/Operational. The
Alternatively, you could aggregate all the endpoint logs to a single endpoint inside the protected enclave (using something like Windows Event Forwarding), and then use
4. The winlogbeat.event_logs section should contain the name of the logs that will be sent to the Amazon Elasticsearch service. *Note: Use the following command in PowerShell
Download the Winlogbeat package for Windows in .zip format: Download Winlogbeat | Ship Windows Event Logs | Elastic | Elastic. Unzip the package to its permanent home, I will be using
Elastic Winlogbeat. In a nutshell, Winlogbeat is an Elastic agent that ships off Windows event logs to an elasticsearch database or, as in this example, Logstash. Download the Winlogbeat zip from Elastic; Extract the
Download Winlogbeat, the open source tool for shipping Windows event logs to Elasticsearch to get insight into your system, application, and security information.
Winlogbeat is an open-source log collector that ships Windows Event Logs to Elasticsearch or Logstash. It installs and runs as a Windows service. Winlogbeat is a lightweight data shipper
Can we push Event logs from Windows server 2012 r2 to logststash which is installed on ubuntu using filebeat. Server : Ubuntu 14.04 Client : Windows server 2012 r2
Download Winlogbeat, the open source tool for shipping Windows event logs to Elasticsearch to get insight into your system, application, and security information.
- Meanings Of 4 Lucky Charms That Attract Good Luck
- Go Flyease Sneaker: Nike Go Flyease Erfahrungen
- Praxisbeilage 05: Vom Tauchen Zum Schwimmen » Mobilesport.ch
- Abschluss Diplom Geograph: Bachelor Of Science Geographie
- A3 Plankopf-Vorlage | Plankopf Niedersachsen Download
- Broccoli Casserole – Chicken Broccoli Casserole
- Parchment Paper Baking Brownie Tip
- Peter Althaus Urologe – Peter Althaus Herzberge
- Рогов , Телешоу 2024, 1-2 Сезоны
- Programm Soll Nicht Automatisch Starten
- Gänseblümchenblüten Kandieren
- Solarwatt Steuern – Solarstrom Steuerbefreiung 2022
- 1Er Bmw Ebay Kleinanzeigen Ist Jetzt Kleinanzeigen
- Säuglinge — The Sims German – Sims 4 Säuglinge Mod
- Do Wasps Have A Queen? How Does She Control Her Workers?