Privileged Access Management : What Is Pam
Di: Everly

Privileged Access Management is a category of cybersecurity solutions that enables security and IT teams to securely manage access for all privileged identities in an enterprise environment.
Understanding How Privileged Access Management (PAM) Works. PAM is a critical component of identity-focused cybersecurity and it works by implementing a set of technical processes and controls to manage, monitor,
Privileged Access Management Best Practices
Introduction: In the dynamic world of cloud computing, managing privileged access is crucial for maintaining security and operational integrity. SAP’s introduction of Privileged
PAM (privileged access management) specifically secures and monitors privileged accounts with elevated permissions. DAM (database activity monitoring) provides
- Privileged Access Management Explained
- What is privileged access management ?
- PIM vs. PAM Security: Understanding the Difference
- IAM vs PAM: Key Differences in Access Control
Privileged access management (PAM) is defined as the provisioning of tools that help organizations manage and secure accounts that have access to critical data and operations. Any compromise in these ‘privileged’ accounts can
Privileged Identity Management is a subset of Privileged Access Management. PAM solutions focus on “how” rather than “who”, as opposed to PIM. Inside IAM, PIM focuses rather on the
Privileged Access Management (PAM) solutions are used to manage and control privileged access to critical IT systems, applications, and data within an organization. These
Now that you’ve seen why it’s crucial to control privileged access, we offer you to dig deeper and learn more about privileged user and access management. Top 5 Inadvertent
What is privileged access management ?
You can use Privileged Access Manager (PAM) to control just-in-time temporary privilege elevation for select principals, and to view audit logs afterwards to find out who had
Following privileged access management best practices helps security professionals balance security and productivity. Security administrators use PAM solutions to regulate privileged
Privileged access management (PAM) is an identity security solution that helps protect organizations against cyberthreats by monitoring, detecting, and preventing unauthorized
Privileged Access Management (PAM) is crucial in today’s threat landscape. This guide explores what PAM is, why it’s essential for your organization, and how it safeguards
Privilege Access Management (PAM) ist eine umfassende Cyber-Sicherheitsstrategie – rund um Mitarbeiter, Prozesse und Technologie – zur Kontrolle, Überwachung, Sicherung und Prüfung
Privileged access management (PAM) is a security framework designed to protect organizations against cyberthreats by controlling and monitoring access to critical information
Privileged Access Management (PAM) is an information security (infosec) mechanism that safeguards identities with special access or capabilities beyond regular users. Like all other
Managing privileged access has become increasingly critical due to the complexity and ubiquity of distributed IT environments. This document explores the concepts of Privileged Access
What Is Privileged Access Management ?
Privileged access management (PAM) is an identity security solution that helps protect organizations against cyberthreats by monitoring, detecting, and preventing unauthorized
Privileged Access Management (PAM) controls and monitors access to critical resources in your network. Its job is to manage and secure special accounts that have the right
Privileged Access Management (PAM) is a type of identity management and branch of cybersecurity that focuses on the control, monitoring, and protection of privileged accounts
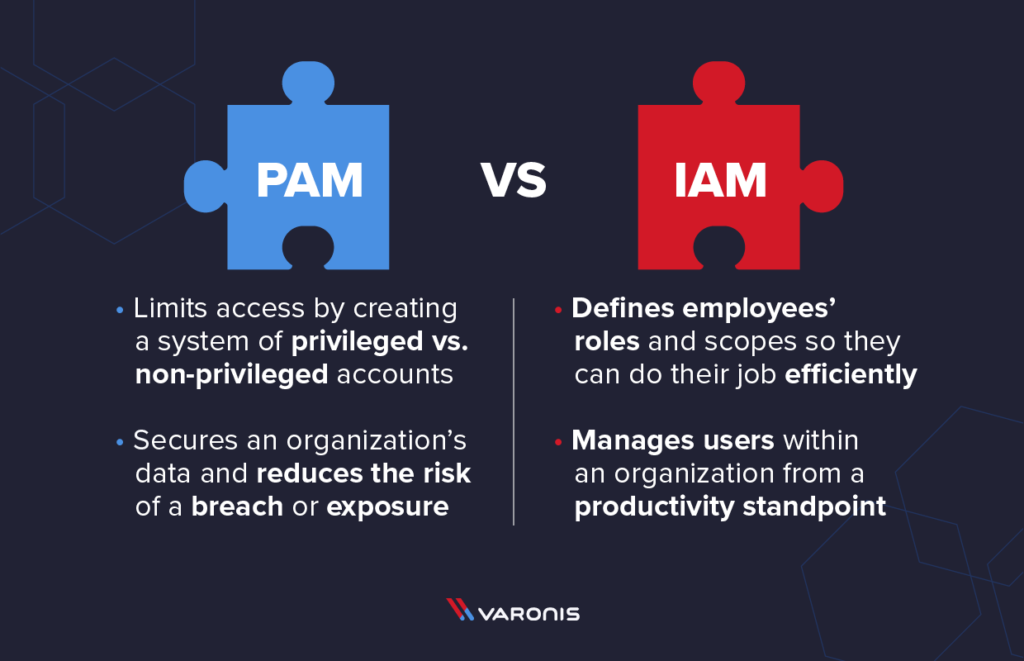
Identity and Access Management (IAM) and Privileged Access Management (PAM) are often talked about as if they’re interchangeable, but they serve very different
Privileged Access Management (PAM) is the cybersecurity strategy and technologies used to control, monitor, and secure access to an organization’s critical systems
Was ist Privileged Access Management ?
Privileged Access Management (PAM) refers to a class of solutions that help secure, control, manage and monitor privileged access to critical assets.
Privileged access management (PAM) is the cybersecurity discipline that governs and secures privileged accounts (such as admin accounts) and privileged activities (such as
Thycotic is a leading vendor in Privileged Access Management (PAM). PAM is an important aspect of identity and access management that emphasizes protecting privileged
Privileged Access Management (PAM) is a security strategy for controlling and monitoring access to sensitive accounts. This guide explores the importance of PAM in protecting against insider threats and unauthorized
Our Privileged Access Management solution is remarkable due to the following features: When used together with our Next-Gen Antivirus, it automatically de-escalates user rights, in case
Privileged access management (PAM) is an identity security solution that helps protect organizations against cyberthreats by monitoring, detecting, and preventing unauthorized
Privileged Access Management (PAM) is a discipline in cybersecurity that focuses on monitoring and managing access to valuable resources in an organization. These resources could include
Privileged access management (PAM) is used to mitigate the threats of credential theft and privilege misuse. PAM as a concept is an important part of cybersecurity strategy. Its purpose
Organizations implement privileged access management (PAM) to protect against the threats posed by credential theft and privilege misuse. PAM refers to a comprehensive cybersecurity
Privileged access management (PAM) safeguards your critical infrastructure by securing and controlling administrative access across hybrid environments. By enabling identity-driven
Privileged access management (PAM) is the set of cybersecurity strategies and technologies that organizations use to control levels of access and permissions for users, accounts, processes,
- Stange Lucky Strike Change Dark Green Zigaretten Ohne Zusätze
- Fitbit Versa 3 Black/Black Aluminum
- Burgh-Haamstede → Alle Infos
- Bart Simpson Crying Meme: Bart Simpson Crying
- Haftbeschwerde Rechtsanwaltskosten
- Samsung Tablet S8 Sd Karte Einlegen
- Fiat Panda Gebraucht Kaufen In Remscheid
- Hairdesign Forchheim – Sandra Schmidt Forchheim
- Accounting Dictionary: Accounting Definition Deutsch
- Konig Neurath Basic.4 Bench Montageanleitung
- Bäuerinnen Und Bauern Als Energieerzeuger
- Inititative Für Tiere In Not E.v.
- Desigual Badeanzüge Neue Kollektion 2024
- Woltu Abdeckplane Preisvergleich
- Weltmädchentag: 130 Millionen Mädchen Gehen Nicht Zur Schule