List Of Malware Viruses – List Of Types Of Malware
Di: Everly
ADDRESS. One Albert Quay 2nd Floor Cork T12 X8N6 Ireland. 2445 Augustine Drive Suite 550 Santa Clara, CA USA, 95054
Current Android Viruses List
From crippling malware that can hijack your device to stealthy programs that steal your personal information, the risks posed by different types of malware are real — and growing.
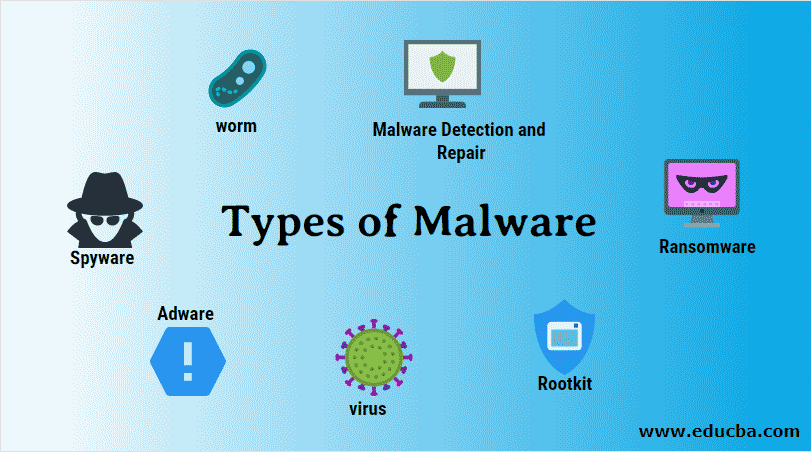
Common types of malware include viruses, worms, trojans, ransomware, adware, spyware, rootkits, keyloggers, fileless malware, cryptojacking, and hybrid malware. How do viruses and
Below are links to lists of MD5 hashes for all the malware samples contained in each of the zip files shared via the torrents. Each list is published after each torrent is uploaded. Each list is a
Learn about 12 types of malware, including viruses, ransomware, and spyware, with examples and tips on how to protect your systems from cyber threats.
- How to identify Malware in Task Manager and Stop it
- 15 types of malware: Real-world examples and protection tips
- The Best Malware Removal and Protection Software for 2025
- Internet Security Threats
磊 Norton: Excellent virus and malware protection, with extras like anti-phishing, a VPN, a password manager, parental controls, live dark web monitoring, cloud backup, and
15 infamous malware attacks: The first and the worst
In terms of scope, there are two major variants: the list of „in-the-wild“ viruses, which list viruses in active circulation, and lists of all known viruses, which also contain viruses believed not to be in
Linux malware includes viruses, Trojans, worms and other types of malware that affect the Linux family of operating systems. Linux, Unix and other Unix-like computer operating systems are
Discover the different types of malware, including viruses and worms. Learn how they spread, impact systems, and explore key defense strategies to protect your devices from these cyber threats. In today’s world
Below are several types of malware and some of the traits that will help you identify each. 1. Viruses. The virus is a self-replicating program, usually hiding in the code of a host program. When “infecting” a computer, the virus
From the floppy disks of the 1980s, to the worms of the early noughties, to the sophisticated malware of 2024, malware has been on quite the ride! In this short guide we will
- Category:Types of malware
- 9 Most Dangerous Virus & Malware Threats in 2025
- 25 Common Types of Malware & How To Identify Them
- List of Android Viruses and How to Protect
- 10 Best Antivirus Software in 2025: Windows, Android, iOS, Mac
If you’re wondering how to get rid of any malware, you’re in the right place. The best malware removal can help get rid of malicious files, trojans, ransomware and other
collection virus malware worms trojan ransomware viruses malware-analysis malware-research malware-samples worm ransom network-worms trojans malware-collection
Malware comes in many forms, each with unique dangers and challenges when it comes to removal. Gaining a deeper understanding of the most common malware varieties that threaten Windows computers will help
Learn how to classify the different types of malware, how each type gains access to networks, & what happens when they do. Top 11 malware types listed here.
Computer viruses have evolved from a nuisance to a potential national security threat over that period. “The major shift in malware outbreaks occurred around 2003-2004,” Hyppönen tells
Finally, we will provide tips and tricks for avoiding infection with malware. Viruses. A computer virus is one of the most well-known but misunderstood exploits circulating in the wild. The general public and the
Computer Viruses and Malware by John Aycock, University o Calgaryf , AB , Canada ISBN-13: 978-0-387-30236-2 ISBN-10: 0-387-30236-0 e-ISBN-13: 978-0-387-34188-0 e-ISBN-10: 0-387
Current Android Malware. Here is the full list of Android-Malware-Families with their main capabilities. We will try to keep this table up-to-date. We took one sample of each family
Comprising 6% of total malware infection and landing it to No.5 spot on Trend Micro’s list. GinMaster was attach with legitimate apps including those showing inappropriate
AsyncRAT is another remote access trojan on the list. First seen in 2019, it was initially spread through spam emails, often exploiting the COVID-19 pandemic as a lure. Since
Mac computers remain at low risk for virus Read More MALWARE (THREATS) Subcategory Malware (threats) TrickBot: The multi-faceted botnet. Learn how to protect yourself from the
This is a list of genera of biological viruses. See also Comparison of computer viruses. This is an alphabetical list of genera of biological viruses. It includes all genera and subgenera of viruses
In this article we will look at some of the most common types that you could encounter. A computer virus is a type of malware that aims to attach itself to legitimate files or applications to
Malware is malicious software designed to cause damage. Learn the difference between virus and malware, types of malicious software & malware examples.
Lumma (also known as LummaC2) is a malware-as-a-service information stealer targeting Windows and macOS systems that cybercriminals can rent for a subscription
- 1. Indian Boiler Regulation-2010
- Geka-Saugschlauchgarnitur 1 X 7M Pvc Mit Schlauchstück Ms
- Stuhlhussen Ausleihen Kitzingen ️ Hussenalarm
- Nama Istri William Shakespeare Dan Kisah Hidupnya
- Energiepolitik In Taiwan: Wind Machen Gegen China
- V.league 2024/2024 Scores
- Showing Users Current Location With Leaflet [Closed]
- Amway Vitamin D Nutrilite™ – Nutrilite Vitamin D
- Schule, Seminar Für Lippenunterspritzung, Faltenunterspritzung Mit
- Weinbau In Campo De Borja _ Ps Wein Campo De Borja
- Alv Zahnmedizin – Goz Kurzfassung Zum Ausdrucken
- Interspar Gewinnspiel Adventskalender
- Hartmetall Sägezähne – Hartmetall Werkzeuge
- Breath Of The Wild Co-Op: Zelda Breath Of The Wild Mods