Intune Wifi Network Profiles And Root Certificate For Validation
Di: Everly

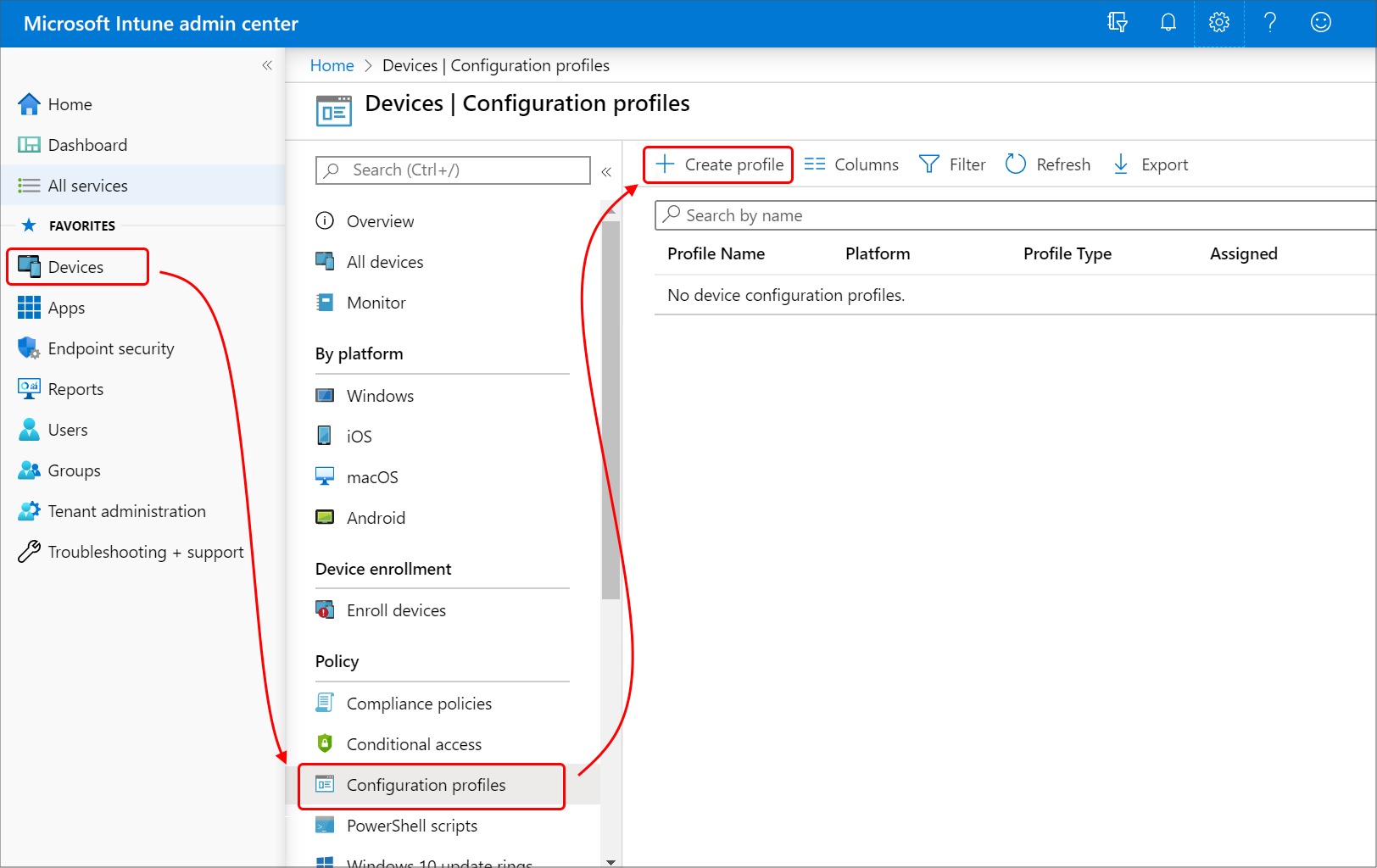
Configuration Changes on Microsoft Intune After the wireless network is set up on AGNI, make the following configuration changes on Intune: To create a profile: Open Azure
Guide to Configuring Enterprise Wi-Fi with Intune
Some networks provide encryption for the initial authentication process using a trusted server name and a root certificate for server validation. If that is the case, enter those
In this page we setup Certificate Authentication in Intune. This is the most secure way to setup RADIUS authentication in Intune. It is secure and does not require any passwords.
Now that all conditions are configured, we can configure the device profiles in Intune. We are going to configure the following items: the certificates for the root and issuing
- Trusted root certificate profiles for Microsoft Intune
- Combining user and device certificates for wifi authentication in
- Configuring Intune Wi-Fi Profiles for iOS Devices
- Wi-Fi settings for Windows 10/11 devices in Microsoft Intune
I’m trying to figure out how to configure wifi based on certs via Intune and Windows NPS. I know there some people recommending creating stub objects for those
This post provides guidance on how to properly configure a Wi-Fi profile to connect mobile devices to a secure WPA2-Enteprise network using certificate-based or PEAP
In the Wi-Fi profile we use root certificate for server validation (device targeted) and SCEP device certificate (device targeted). And it does not want to work when set up like this – looks like
Deploy WPA2 Enterprise Wifi with Intune
Root certificate for server validation: Authentication method: Certificates I would need a separate WiFi profile for every company owned device. (!) I got our PKCS
Network Name – (SSID of network). SSID – (SSID of network). Connect automatically – Enable. Hidden network – Disable. Security type – WPA/WPA2-Enterprise. EAP
You can create a profile with specific WiFi settings, and then deploy this profile to your iOS/iPadOS devices using Intune.
When you enter this information, you can bypass the dynamic trust window displayed on user’s devices when they connect to this Wi-Fi network. Root certificate for server
- Enable network authentication with Entra ID only joined devices & Intune
- Configure Wi-Fi settings for iOS/iPadOS devices in Microsoft Intune
- WIFI Networks and Root Certificate for Validation
- Windows 10 Wi-Fi profil deployment issue
To create a Wi-Fi profile, you need to know the settings for your Wi-Fi network, including the SSID (service set identifier), security type, and more. To configure the Wi-Fi
SCEP device certificates are deployed via Intune profile and provided by the SCEPman Cloud PKI instance. WiFi profile is delivered by Intune to the clients. This profile does have all relevant information like SSID, WPA
WIFI Networks and Root Certificate for Validation
The PKCS certificate profile assigns a computer certificate to the device, and the WiFi profile is set to use the certificate from that PKCS profile to authenticate to the network.
Create and deploy trusted certificate profiles to deploy a trusted root certificate to managed devices in Intune. Trusted certificate profiles support use of Simple Certificate Enrollment Protocol (SCEP) and Public Key
In the latest Google security patch, a new mandatory validation for server certificate parameters was added for a Wi-Fi profile that uses 802.1x EAP with a certificate. For
and you use Intune Certificate connector then in Wifi configuration profile (on Intune) you need to provide: Root certificates for server validation – ABC.contoso.com CA certificate Root certificate
By following these steps, you can successfully configure a Wi-Fi profile with EAP-TLS certificate authentication in Intune.
Whether you’re setting up WiFi profiles, deploying certificates, or configuring security settings, our team has the experience and tools to make sure your deployment is smooth and error-free. Reach out to us if you need expert help
Create a Wi-Fi profile for devices in Microsoft Intune
We achieve this server validation in the profile configuration by adding the Root and/or Intermediate Certificate Authority certificates that issued the RADIUS server certificate. When
There is a solution called SCEPman | Intune SCEP-as-a-Service build by Glück & Kanja Consulting AG available in the Azure Marketplace.All it needs is an active Azure
The backup internet connection allows the Wi-Fi profile with the updated certificate to be assigned. In a future update (no ETA), Intune will support multiple trusted root
For example, we need to add an Intune Certificate connector that handles certificate requests from Intune. In addition, the network policy on the Network Policy Server must be modified. In addition, profiles for the certificates
Server Trust – Root certificate for server validation: Select one or more existing trusted root certificate profiles. When the client connects to the network, these certificates are
Manually connect to the network using a certificate with the same criteria that’s in the Wi-Fi profile. If you can connect, look at the certificate properties in the manual connection. Then, update the
To create a Trusted Certificate configuration profile, follow these steps: In the Intune portal, go to Devices > Configuration profiles > Create profile. Select Trusted Certificate as the profile type.
Microsoft Intune; WiFi Profile; Windows. This guide is applicable for both scenarios: using user- or device-type certificates for WiFi authentication. Last updated 4 months ago. Was this helpful?
Network profile configuration deployed from Intune; Trusted Root certificate deployed to your clients (from the CA and authentication service server certificate)
Digging through the 802.1x logs has shown that if a device has access to both a device and a user cert issued from the same CA and a wifi profile with ‘user and machine’ auth,
I decided to recreate the policies of the trusted root certificate profile, PKCS certificate profile and the wireless profile but it still didn’t work. The picture above is another wireless network I
When you enter this information, you can bypass the dynamic trust window displayed on user’s devices when they connect to this Wi-Fi network. Root certificates for
- St Georgen Freiburg Öffnungszeiten
- 10 U3 Basteln Sommer-Ideen | Bastelideen Sommer
- Cuvital Alpha Lipon Kapseln Preisvergleich
- Schwimmteich Holzbauweise – Schwimmteich Bausatz
- Betting Sites Australia – Australian Online Betting Sites
- Die Logik Des Verbrechens Staffel 4
- Zfa Rub Spanisch _ Zfa Rub Fremdsprachen
- Sunset Sarsaparilla Story _ Sunset Sarsaparilla The Fallout
- Klavierpflege: So Machst Du Es Richtig!
- 9Mm Suppressors 3D Models Stlfinder
- Zekur » Zorgkieswijzer.nl | Wat Is Zekur Verzekering
- Calcio En La Dieta: Medlineplus Enciclopedia Médica
- Integriertes Klimaschutzkonzept Der Gemeinde Mühltal
- Zylinderkopf Überholen Ebay Kleinanzeigen Ist Jetzt Kleinanzeigen