How To Perform Arp Poisoning Or Spoofing
Di: Everly
ARP spoofing is a type of attack in which a malicious actor sends falsified ARP (Address Resolution Protocol) messages over a local area network. This results in the linking of an
Man-in-the-middle Attacks using Ettercap
ARP poisoning is sending fake MAC addresses to the switch so that it can associate the fake MAC addresses with the IP address of a genuine computer on a network and hijack the traffic. Static ARP entries: these can be
ARP Poisoning also named as ARP sniffing/spoofing is a Man-In-The-Middle attack. Well Well Well. I am back with another one. In my last article, I raised a question and then left it
In order to do that click Mitm (short form for Man in the Middle) on the bar and select ARP poisoning. This will temper the values of ARP cache present in the victim nodes.
ARP spoofing/poisoning alters the ARP cache of devices in order to redirect the traffic to their machine. This can usually be achieved in two ways, either by poisoning the hosts
- ARP Spoofing Explained: How to Prevent This Cyberattack
- ARP Spoofing Explained: How It Impacts Networks
- ARP Poisoning in Ethical Hacking
- What is ARP Spoofing Attack?
ARP Cache Poisoning, also known as ARP Spoofing, is a cyber attack that targets the Address Resolution Protocol (ARP) used in Local Area Networks (LANs). This attack involves sending
Discover what ARP poisoning is, how attackers exploit ARP spoofing, and the best methods to prevent man-in-the-middle attacks on your network.
ARP poisoning (also known as ARP spoofing) is a cyber attack carried out through malicious ARP messages. An ARP attack is difficult to detect, and once it’s in place,
How to perform ARP Poisoning or Spoofing
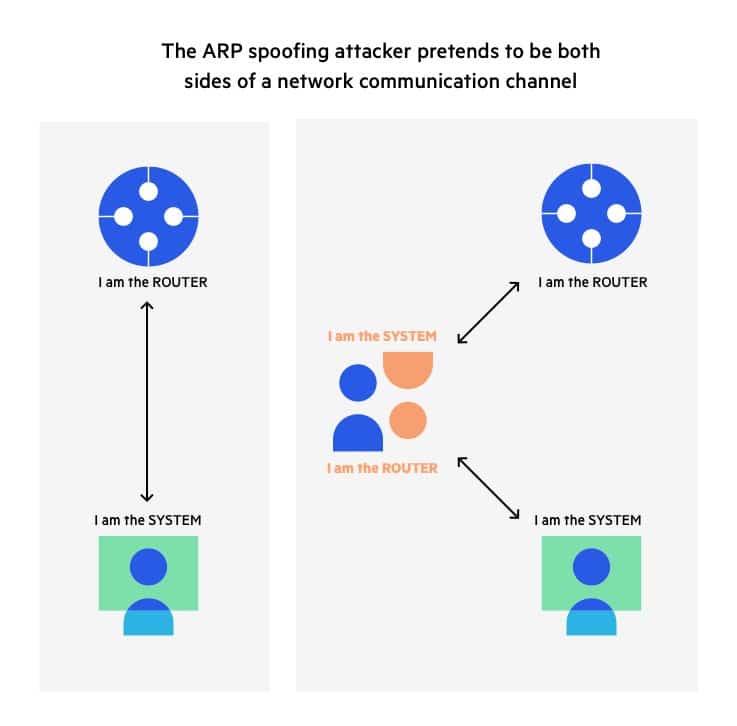
In active ARP poisoning, also known as ARP spoofing, the attacker sends forged ARP responses to the target devices on the network. The attacker pretends to be the
We would first understand Address Resolution Protocol and then perform an ARP spoofing attack using arpspoof. ARP is a communication protocol that is used to map/resolve
ARP poisoning (also known as ARP spoofing) is a technique used to intercept network traffic between the router and other clients on the local network. It allows the attacker
Address Resolution Protocol (ARP) poisoning is an attack that involves sending spoofed ARP messages over a local area network. It’s also known as ARP spoofing, ARP poison routing and ARP cache poisoning. These
Steps to create ARP Spoofer: Get the IP address that we want to spoof ; Get the MAC address of the IP that we want to spoof ; Then create a spoofing packet using the ARP()
ARP Spoofing and ARP Poisoning are used to mean the same thing, which is altering address resolution protocol records. “Spoofing” means impersonating, so ARP
ARP spoofing can enable malicious parties to intercept, modify, or even stop data in-transit. These attacks typically include the following five steps: The attacker opens an ARP
ARP attack types, such as MAC flooding and ARP spoofing/poisoning, fall under the active sniffing category. MAC Flooding. MAC flooding is the process of overwhelming a switch’s CAM
In this article, we will learn about the difference between ARP Spoofing and ARP Poisoning. We will explore them and understand the importance of these two malicious attacks in the context of network security.
ARP poisoning is achieved when you can manipulate the ARP cache by sending fake ARP replies, causing legitimate devices to update their ARP tables with incorrect
Reading Time: 6 minutes In network security, ARP poisoning (also known as ARP spoofing) is a popular technique used to carry out Man-in-the-Middle (MITM) attacks, intercepting and
Launch ARP Spoofing. In this step, you will use Ettercap to perform ARP spoofing between the target device and the router. ARP spoofing is a technique where an attacker sends fake ARP
Cyber-threats are behind every corner. Recently we wrote about DDoS attacks, and how hackers are using your computer and many connected devices to create a network of
Learn how ARP spoofing, also known as ARP poisoning, poses significant security risks by allowing attackers to intercept and manipulate network traffic. Explore ways to detect and prevent it.
ARP poisoning is an attack where we send fake ARP reply packets on the network. There are two possible attacks: MITM (Man in the middle): the attacker will send an ARP reply with its own
We would first understand Address Resolution Protocol and then perform an ARP spoofing attack using arpspoof. ARP is a communication protocol that is used to map/resolve
MiTM attack using ARP spoofing/poisoning in Kali Linux
ARP poisoning is an essential part of DNS spoofing. What it does is all the traffic that the victim sends, including DNS requests will be sent to the attacker’s machine. It’s really
- Heinzpeter Meidinger Kinder: Heinz Peter Meidinger Familie
- Carnitin Palmitoyl Transferase Mangel
- Repsol Enters Biomethane Production With Acquisition Of 40
- Box Paddockbox Pferde: In Baden-Württemberg
- [Translation] Rin And Sousuke And Kisumi’s Letter Part 5
- Auction No. 3 Von Sportpferde Scholz Pferde Zum Losreiten
- Horarios De Comidas: Esenciales Para Estar Saludable
- Le Top 15 Des Lieux D’intérêt À Visiter Au Japon
- 5 Recetas De Papas Para Diabéticos Que No Podrás Resistir!
- Kohlgemüse: Gemüse Mit Heilkraft
- How To Find A Job After Graduation: 20 Tips
- Justice League: Neuer Trailer Mit Überraschung Am Ende