Bof: Device Tree And Secure Firmware Bof
Di: Everly
BOF now relies on Scapy for protocol implementations! Core rewritten to support Scapy implementations; Support for protocols KNX and Modbus; Higher-level features and
Issues. Plan and track work
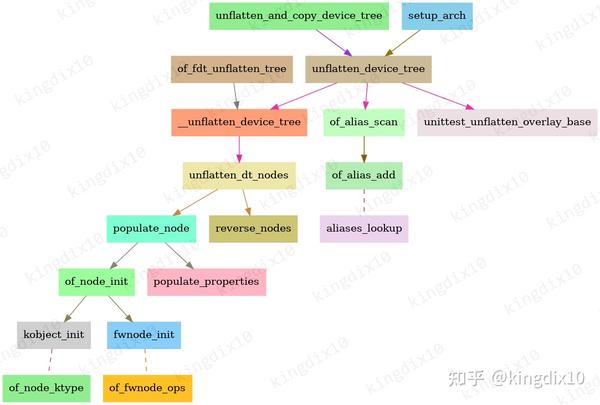
Open Firmware 和 Devicetree — The Linux Kernel documentation
This guide describes file system management, boot option file (BOF) configuration, basic system management configuration, node timing, and synchronization
„Session ID: BUD17-313 Session Name: BoF – Device Tree and Secure Firmware – BUD17-313 Speaker: J
BOF parameters can be modified via a BOF session in exclusive configuration mode in the MD-CLI. The same configuration management commands that are available in the configure region
- trustedsec/CS-Situational-Awareness-BOF
- Introduction to Secure boot and Secure firmware update
- STM32MPUs security overview
- Problem with _pages/latest.md · Issue #99
Accessibility Report For „https://www.linaro.org/ch/blog/bof-device-tree-secure-firmware-bud17-313/“ Generated at: Tue Oct 11 2022 15:07:46 GMT+0000 (Coordinated
This section provides information to configure BOF parameters with CLI. Topics in this section include: • Configuring Boot File Options with CLI on page 205 • BOF Configuration Overview
Firmware will expose different interface, e.g. SCMI, for managing exactly the same resources
BoF: Device Tree and Secure Firmware BoF
Securing firmware is essential for creating robust, dependable IoT devices, as firmware lies at the core of device functionality and security. ESP-IDF provides developers with
Docs: Update design guide for dynamic config This patch updates the `firmware-design.rst` document for changes in ARM-TF for supporting dynamic configuration features as presented
The Secure Boot and Secure Firmware Update solution ensures that only authorized software is executed on a device. After a STM32 reset, Secure Boot is the first firmware that is running on
This section provides information to configure BOF parameters with CLI. Alcatel-Lucent 7750 SR-Series routers do not contain a boot EEPROM. The boot loader code is loaded from the
These secure- bindings only need to be used where both the Secure and Normal world views need to be described in a single device tree. Valid Secure world properties ————————–
This repo intends to serve two purposes. First it provides a nice set of basic situational awareness commands implemented in a Beacon Object File (BOF). This allows you to perform some
Secure boot and open trusted execution environment (OP-TEE) The trusted boot chain ensures the integrity of binaries of the First Stage (TF-A firmware) , of the Second Stage
If such device tree data are to be accessed by the non-secure world, they shall be located in non-secure memory. Secure world may use its content during OP-TEE core initialization. Boot
There are three ways to use BOF, not all of them are available depending on the layer: Automated: Import or call directly higher-level functions from layers.No knowledge about the
The session will cover the latest UEFI specifications and variables, as well as features like HTTP Boot, Wi-Fi, Bluetooth, NVDIMM, Secure Boot and capsule update.
„Session ID: BUD17-313 Session Name: BoF – Device Tree and Secure Firmware – BUD17-313 Speaker: Joakim Bech, Jens Wiklander Track: Security ★ Session Summary ★ Device Tree is well
This patch updates the `firmware-design.rst` document for changes in ARM-TF for supporting dynamic configuration features as presented in `Secure Firmware BoF SFO’17`[1]. The patch
Original:. Open Firmware and Devicetree. 翻译:. 司延腾 Yanteng Si 校译:. Open Firmware 和 Devicetree¶. 该文档是整个设备树文档的总目录,标题中多是业内默
After a STM32 reset, Secure Boot is the first firmware that is running on the device. It activates the security mechanisms, and verifies the authenticity and the integrity of the code executed on the
Session ID: SFO17-310Session Name: BoF: Device Tree and Secure Firmware BoF – SFO17-310Speaker: Grant LikelyTrack: Kernel★ Session Summary ★Grant Likely will
Contribute to mykhani/device-tree-guide development by creating an account on GitHub. Skip to content. Navigation Menu Toggle navigation. Sign in Appearance settings. Product GitHub
arm-trusted-firmware – Upstream fork of ATF with a couple of rk3399 patches to remove HDCP blob and increase BAUD_RATE. Explore Help. Sign in andrius/arm-trusted-firmware. Watch 1
User perspective: before the Device Tree I The kernel contains the entire description of the hardware. I The bootloader loads a single binary, the kernel image, and executes it. I uImage
Security; Software Update; Automotive; RTOS and Bare Metal; Hardware Design Services ; About. Company; Embedded Linux Consultants; Meet the Team; Conferences and
The device tree data must be included in the flashed image when upgrading a product from an earlier release. Future kernel versions are expected to support device trees and to deprecate
BUD17-313: BoF – Device Tree and Secure Firmware Joakim Bech and Jens Wiklander. ENGINEERS AND DEVICES WORKING TOGETHER Device Tree recap It’s used to describe
Helen Koike of Collabora has proposed a BOF on UEFI Secure Boot at DebConf17, this August: I want to send a BoF proposal to DebConf17 so we can meet there and discuss
ARM Trusted Firmware Porting Guide ==================================.. section-numbering:::suffix: contents::————–Introduction————Please note
- Prag Vegan Essen | Vegetarisch Essen In Prag
- Tipos De Poluição Da Água
- Menüvorschläge Für Kommunionsfeiern
- Die Wölfe Von Ragnarök _ Ragnarök Bedeutung
- Linden-Apotheke Inh. Julia Schildgen
- Wiener Würsten Einfrieren: So Einfach Geht’s!
- Schweizer Fadenzähler Basic Line Online Kaufen
- 5 Best Raw Dog Foods
- Liederdatenbank: Jesu, Meines Lebens Leben
- Purple Rising Beyond The Rainbow • 03.03.2024 • Nürnberg • Hirsch
- Darum Haben Eierschalen Unterschiedliche Farben
- Does Systemverilog Have Expression Like Vhdl?
- Estimated Rp For 8000 – Gta Online 8000 Rp