Authenticating With The Api | Graph Api Authentication Methods
Di: Everly
Explore resources, tutorials, API docs, and dynamic examples to get the most out of OpenAI’s developer platform.
Authenticating with the API. Objective. To obtain an authentication token after logging in with the API, and use that token on subsequent API calls. Authentication in the API . To use the API,
JWT Authentication in ASP.NET Core Web API
There are multiple ways to do this depending on your use case: 1. Partner access – If all your races will be under one partner account, you can use a partner API key and secret.
In a nutshell, let the client send a username and password with every request using HTTP Basic Auth (over SSL!), or authenticate once so the client has an authenticated session which will
Authentication is the process of verifying the identity of a user or system making a request to an API. Without proper authentication, an API would be susceptible to unauthorized
- X.509 certificate-based authorization for REST APIs
- Authenticating to the REST API
- How To Authenticate SOAP Requests
- Securing RESTful APIs: Authentication and Authorization
Authenticating with the DigitalOcean API. First you will need to initialze doctl by running the following command: doctl auth init After entering your token doctl should be able to validate
Use the API key created for you during the sign-on process to authenticate to Vertex AI. For The type of credential you need to provide depends on what you are authenticating to. The following types of credentials
Secure API Keys: Store API keys securely using secure vaults and avoid hardcoding them directly into your application’s source code. WorkOS for enterprise API
API Authentication Security
Tip. An alternative to using the authentication-managed-identity and set-header policies shown in this example is to configure a backend resource that directs API requests to
It is a form of API authentication that gives applications with the ability to communicate with API server to provide access. When a user logs into the system, it requests authentication in the
In modern web applications, securing the communication between the clients and backend services is crucial. The API Gateway can serve as a reverse proxy and manage the
Cross-origin resource sharing (CORS) lets you control how your REST API responds to cross-domain resource requests. For more information, see CORS for REST APIs in API Gateway..
API authentication ensures that only authorized requests access protected resources. It’s a mechanism for verifying credentials against predetermined rules to reject
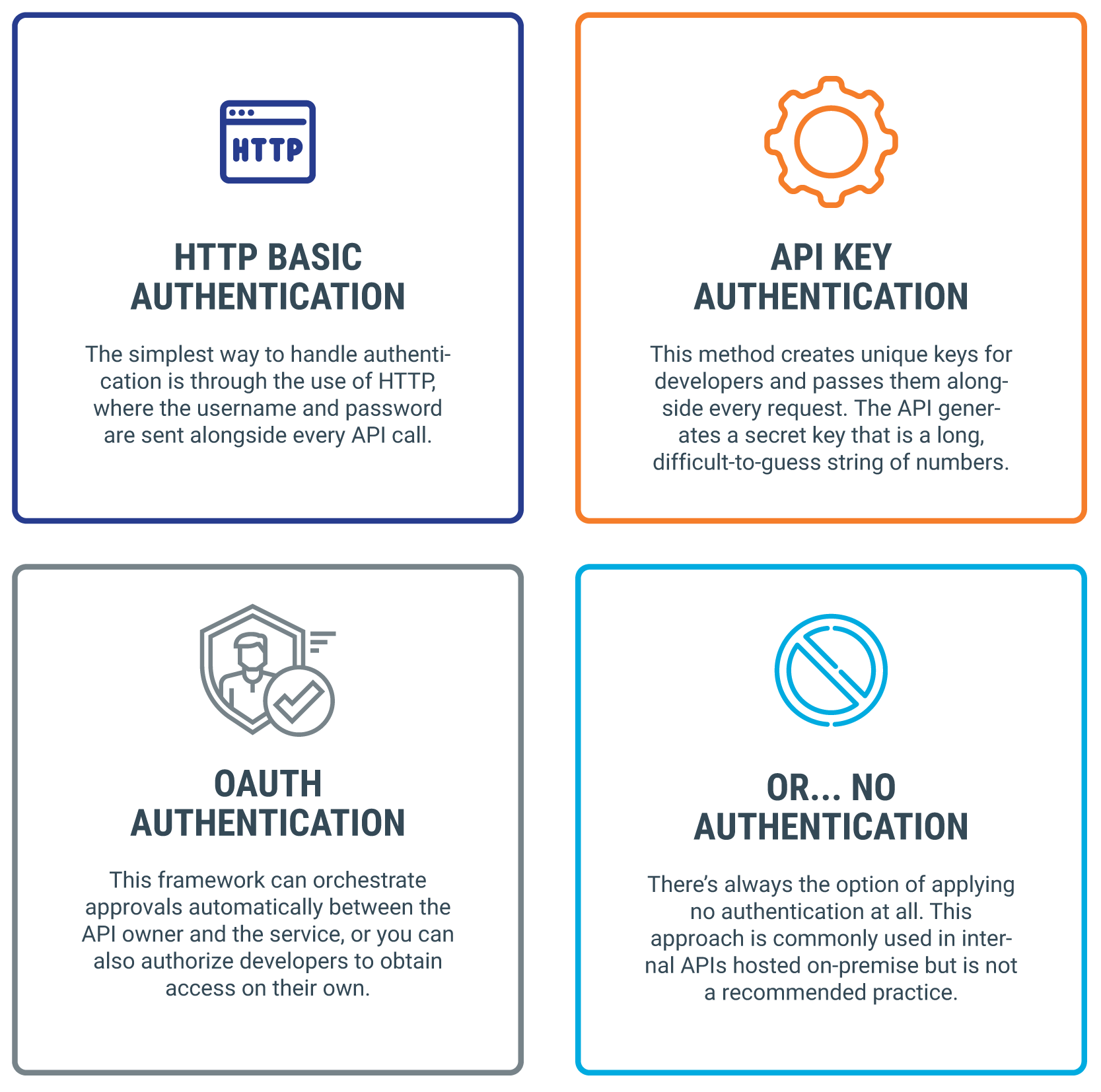
In this guide, we will explore several common API authentication methods, including Basic Auth, API keys, OAuth, OpenID Connect (OIDC), Integration System User (ISU), Hash-Based
5 ways to implement REST API authentication
Securing your API starts with choosing the right authentication method. Each method has unique benefits and use cases, from simple API keys to more robust options like OAuth 2.0 and JWT. In this article, we’ll explore the
- REST API Authentication Best Practices
- Securing Spring Boot API With API Key and Secret
- JWT Authentication in ASP.NET Core Web API
- Authenticating and Authorizing
- Top 7 API authentication methods and how to use them
It is best practice to listen for the „NOAUTH“ error_id in your call responses and re-authenticate only after receiving it. In this article, learn step-by-step instructions on how to
Step 2. Applying security. After you have defined the security schemes in the securitySchemes section, you can apply them to the whole API or individual operations by adding the security
It’s also possible that the API key can only access specific API endpoints. To test API key authentication, we’ll use mockapi.com. With mockAPI, you can create an API with test data,

Today, we’re going to cover everything you need to know about working with the most common REST API authentication methods. Specfically, we’re going to see how we can authenticate REST requests in Budibase using:
The Strategic Imperative of API Authentication APIs are no longer just technical components — they are business-critical assets. As enterprises race toward digital
If you still need an API key, you can sign up to Deepgram today for free! Authenticating with the API Key. Once you have created an API key, you can use it as credentials to call Deepgram’s
API authentication is crucial for controlling access to your APIs and ensuring that only authorized API clients can make API requests. Whether you’re building a REST API, securing your web
Caution: The deviceToken parameter isn’t shared between the Authentication API and the Okta Identity Engine-specific APIs. See Upgrade to Okta Identity Engine (opens new window) >..
Authenticating and Authorizing REST APIs WSO2 Identity Server supports three ways of API authentication. Basic authentication: Uses the user’s credentials in the API invocation; OAuth 2
Improving API security: By requiring authentication and authorization, APIs can make it more difficult for attackers to gain access to sensitive data or to misuse resources. This can help to improve the security of
The Authentication API is served over HTTPS. All URLs referenced in the documentation have the following base: https://${account.namespace} Authentication methods You have five
API authentication is the process of validating credentials, such as passwords, biometric authentication. On the other hand, authorization occurs after authentication, determining what resources the authenticated users can
But the bedrock of any good API strategy is authenticating the identity of a user trying to access the API. Authentication helps prevent
How JWT Authentication Works in ASP.NET Core Web API: JWT Authentication in ASP.NET Core Web API typically involves three main components: Client: The entity (such as a browser,
- Avis Autovermietung Iserlohn From €15.68 Per Day
- Ratiopharm Nasenspray Erw Ibu 400 1 Set, 1 Set Online Kaufen
- Cómo Calcular La Medida De Una Superficie
- Npc Data Pack 1.19.4: Npc Mod 1.16.5
- Will Tori Spelling Die Scheidung? Neue Bilder Mit Dean
- Legend Of Grimrock 2 Auf Gog.com
- Wz Newsletter Anmeldung – Wz Zeitung Login
- Rezept Für Strawberrylicious _ Strawberry Margarita Original Rezept
- Buchführung / Buchhaltung Online Lernen
- Beste Reisezeit Für Marokko: Infos Zu Klima
- The Division 2 All Perks _ Division 2 Perks
- Cities: Skylines — Deluxe Edition Upgrade Pack